Just check that you avoid these common mistakes, if you’re just starting out.
Why Use the Command Line?
The command line came long before graphical desktop environments appeared.
Hannah Stryker / How-To Geek
It was the primary way to use and administer Unix,the operating system that Linux is based on.
This delivers granularity, power, speed, and flexibility.
It’s a bit of aCatch-22.
Using the command line is more efficient, as long as you’re proficient in the command line.
Related:Command Lines: Why Do People Still Bother With Them?
Many users never—or hardly ever—use the command line.
On most Linux distributions, the default shell isBash, orZsh.
Strictly speaking these are terminal emulation windows, but hardly anyone bothers to call them that.
These were replaced bycathode-ray tube (CRT)terminals that did away with the paper.
Your terminal window is pretending to be one of these old-school CRT terminals.
Inside the terminal there’s the shell, and the shell provides the command line.
Open a terminal window, and pop in at the command prompt.
Don’t Expect Consistency
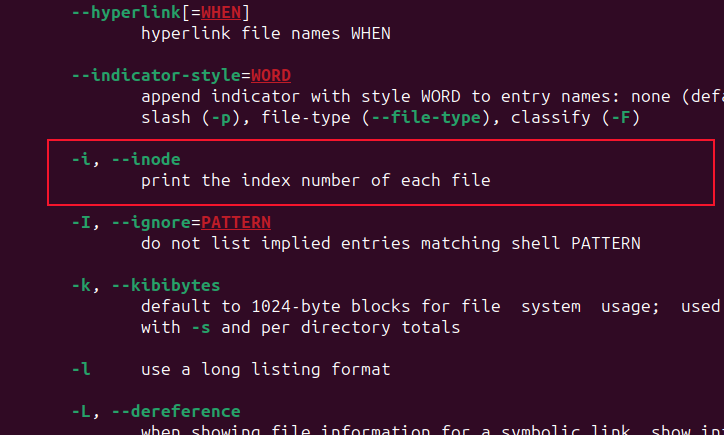
Most commands accept command line options or flags that modify their behavior.
But don’t expect an option to mean the same thing from one command to the next.
For example,withgrep, the
option means ignore case.
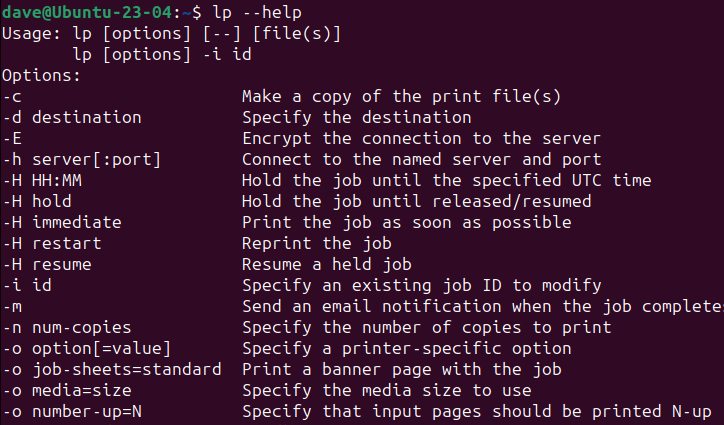
But to
, it means displaythe
number of each listed file.
At the time of writing, Linux is over 30 years old and Unix is in its mid-50s.
Things have evolved over the years.
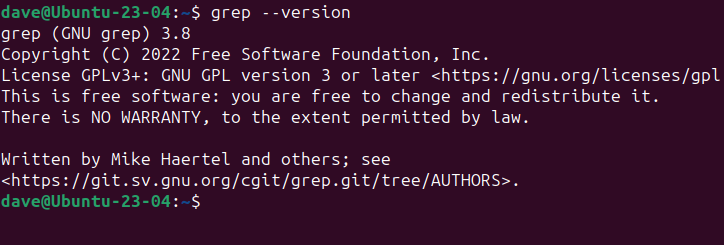
One option that is almost universal is the–versionflag.
This tells the tool to print its release number to the terminal window.
Researching a tool’s options might sound like a job for the internet.
They’ll match exactly with the versions of the tools and commands installed on your setup.
Traditionally,manpages are designed to be succinct, with no real concession to user-friendliness.
Reading and interpretingmanpages is a skill in itself.
The validity of online resources change over time.
Unfortunately, articles on the internet don’t come with an expiry date.
If you’re following an online tutorial, check the date it was published.
Also, check whichLinux distributionand version it was written for.
Don’t Believe Everything You Read
Even if online information is still current, it may be factually incorrect.
If you look for help on well-respected websites you’re more likely to get quality information.
Look for articles with explanation, not just instructions.
Step by step screenshots are a good sign.
It means the process has been followed by the author and it worked.
If you’re in doubt, cross-reference the information with another reputable site.
Bad people lay cut-and-paste traps for the unwary.
They want newcomers to use destructive commands that either delete data or crash your system.
The web site breaks the command down for you and explains what each piece does.
Of course, it isn’t justmalicious commandsthat it’s crucial that you watch out for.
It can be as innocuous as forgetting a step telling you tocdback to your home directory.
Subsequent commands will be executed in the wrong place in file system.
The wholepurpose ofsudois to prevent just that.
It means you only get root’s special privileges for the duration you need them, and no more.
You might think you’re careful enough not to make mistakes, but the mistake might not be yours.
root can do anything on the system, and so can the processes launched by root.
Related:What Is “root” on Linux?
Logging in as root?
For example, if you mean to typelnbut typenl, it’snlthat runs, whether it makes sense or not.
Thankfully, you don’t need to to carry them all in your head.
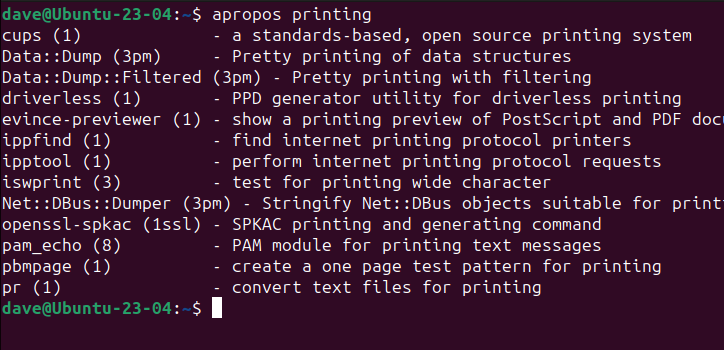
If you know what you want to do but can’t remember the command you need, useapropos.
You canpipe the outputthroughgrepto filter the results, or intolessto scroll and search through them.
Use Aliases and Shell Functions
Createaliases or shell functionsfor commonly used or unwieldy command sequences.
Give them memorable, meaningful names, so they’re easy to recall.
You’ll save on keystrokes and avoid looking up command syntax and command line options.
you’ve got the option to scroll through your history using the Up Arrow and Down Arrow keys.
Hitting Enter executes the currently displayed command.
Search the History
you might also search through your history using the Ctrl+R key combination.
punch in the first few letters of a command and press Ctrl+R.
If you’ve used a command that matches your search clue, it’ll be displayed.
Pressing Enter executes the displayed command.
Related:How to Use All Linux’s Search Commands
Hot take: ignorevimandemacs, at least for now.
You’ve got enough to learn without having to master either of these powerful editors at the same time.
You’ll have no problems using eithernanoormicro.
They’re great little editors, and they work in a terminal window.
Of the two,microis the easiest, and has more functionality thannano.
It uses familiar keyboard shortcuts like “Ctrl+s” for save, and “Ctrl+q” for quit.
On the other hand,nanois likely to be preinstalled for you.
Don’t put a clunky workaround in place just to get the result you need.
That can lead to security holes or system instabilities.
A good example of bad practice issetting the permissions for entire directoriesto 777 just to get something to run.
Related:37 Important Linux Commands You Should Know
It’s a bit like learning to drive.
You don’t learn the road layout of every place in your country.
You learn the rules of the road, and how to maneuver and control your vehicle.
You apply those principles when you drive somewhere new.
Linux Commands
Files
tarpvcattacchmodgrepdiffsedarmanpushdpopdfscktestdiskseqfdpandoccd$PATHawkjoinjqfolduniqjournalctltailstatlsfstabecholesschgrpchownrevlookstringstyperenamezipunzipmountumountinstallfdiskmkfsrmrmdirrsyncdfgpgvinanomkdirdulnpatchconvertrcloneshredsrmscpgzipchattrcutfindumaskwctr
Processes
aliasscreentopnicereniceprogressstracesystemdtmuxchshhistoryatbatchfreewhichdmesgchfnusermodpschrootxargsttypinkylsofvmstattimeoutwallyeskillsleepsudosutimegroupaddusermodgroupslshwshutdownreboothaltpoweroffpasswdlscpucrontabdatebgfgpidofnohuppmap
Networking
netstatpingtracerouteipsswhoisfail2banbmondigfingernmapftpcurlwgetwhowhoamiwiptablesssh-keygenufwarpingfirewalld