Have you ever wondered how they do it?
Heres how they work.
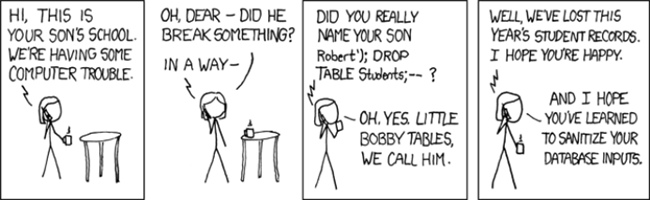
Image byxkcd
Denial of Service Attack
What is it?

How does it work?
The logistics of a DDoS attack may be best explained by an example.
The attackers coordinate so that on Tuesday at 9 AM they will all call Company X’s phone number.
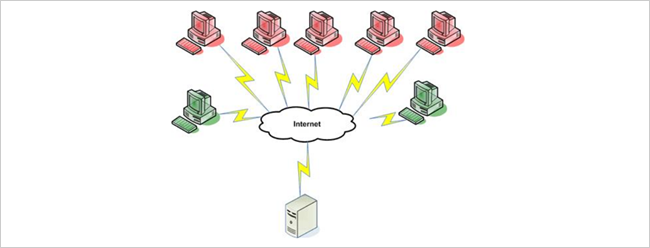
The result is that legitimate customer calls (i.e.
So in essence Company X is potentially losing business due to the legitimate requests being unable to get through.
A DDoS attack on a web server works exactly the same way.
If there is no match, no UserID is returned so the login credentials are invalid.
While a particular implementation may differ, the mechanics are pretty standard.
This act of manipulating the query to produce unintended results is a SQL injection attack.
What damage can be done?
If this isn’t clear now, a few examples should help provide some clarity.
Preventing a SQL injection attack
As we mentioned several times previously, a SQL injection attack is easily preventable.
An SQLI attack is easily thwarted by what is called sanitizing (or escaping) your inputs.
Instead you sanitize it by using the respective database’s escape character.
Let’s assume the escape character for an inline single quote is prefacing each quote with a \ symbol.
So “O’neal” would be sanitized as “O'neil”.
This simple act of sanitation pretty much prevents an SQLI attack.