Quick Links
Thesudocommand gives a user superuser or root powers.
No doubt you gave them the “with great power comes great responsibility” speech.
Here’s how to verify if they listened or not.
fatmawati achmad zaenuri/Shutterstock.com
The sudo Command
Thesudocommand stands for “substitute user do.”
It lets an authorized person execute a command as though they were another user.
The most common waysudois used is to omit the command line options and use the default action.
This effectively executes the command asthe root user.
Only the privileged can usesudo.
Permission to do so is granted to the regular user that you create during installation.
This is the preferred way to handle access to the capabilities of the root user.
This was a dangerous scenario.
Any mistakes you made in the terminal window as root would be executed, no matter how drastic.
Using the root account instead of a regular account is also a security risk.
Related:How to Control sudo Access on Linux
Usingsudofocuses the mind.
You only invoke your superuser status when you should probably do something that needs them.
You don’t want them running commands recklessly or speculatively.
The health and well-being of your Linux installation depend on privileged users behaving respectfully and responsibly.
Here are several ways to monitor their root usage.
The auth.log File
Some distributions maintain an authentication log, in a file called “auth.log.”
With the advent and rapid uptake of
, the need for the “auth.log” file was removed.
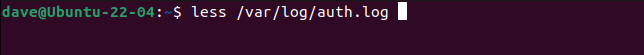
you’re free to pop swing open the file inlesslike this.
This command worked on Ubuntu 22.04.
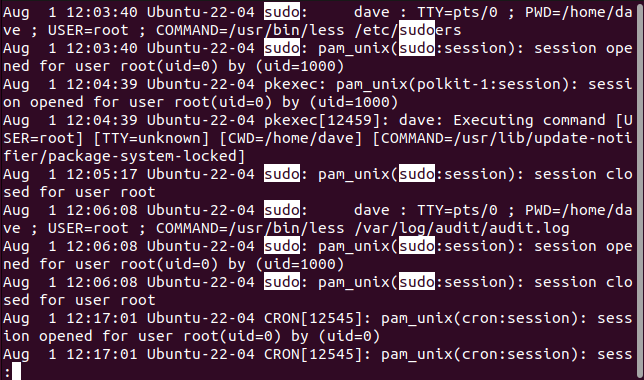
Even using the search facilities ofless, it can take some time to locate thesudoentries you’re interested in.
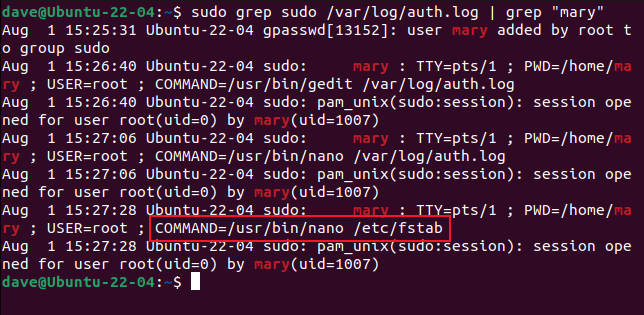
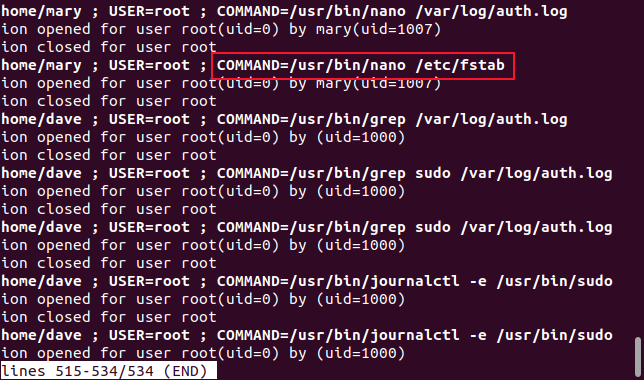
Let’s say we want to see what a user calledmaryhas usedsudofor.
Note thesudobefore grep and before the logfile name.
This gives us lines that have “sudo” and “mary” in them.
We can see that the usermarywas givensudoprivileges at 15:25, and at 15:27 she’s openingthefstabfilein an editor.
Using journalctl
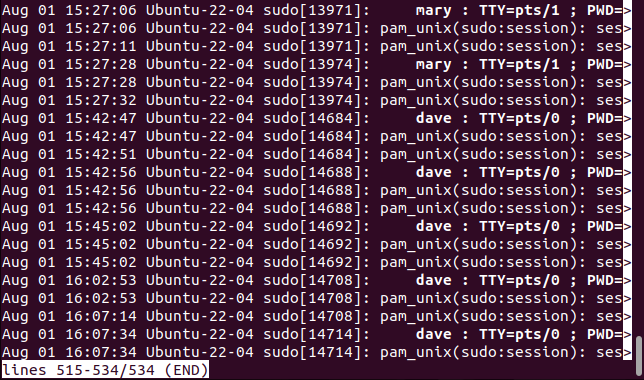
The preferred method onsystmd-based Linux distributions is to use thejournalctlcommand to review system logs.
Becausesudois a binary located at “/usr/bin/sudo” we can pass that tojournactl.
The-e(pager end) option tellsjournalctlto initiate the default file pager.
Usually this will beless.
The display is automatically scrolled to the bottom to show the most recent entries.
The log entries that featuresudoare listed in less.
(Or stretch your terminal window so that it is wider.)
We’ll look at the GNOME logs utility.
punch in “logs” in the search field.
The “Logs” icon appears.
tap the icon to launch the “Logs” program.
Clicking on the categories in the sidebar will filter the log messages by message jot down.
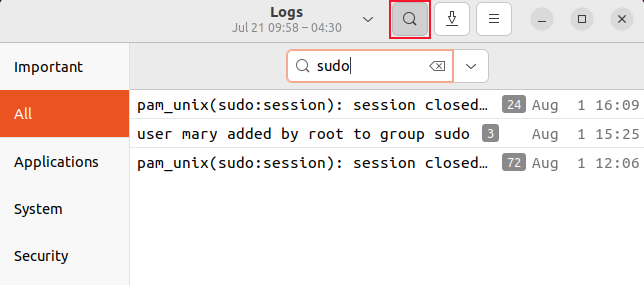
Enter some search text.
We’re going to search for “sudo.”
The list of events is filtered to display only those events that relate to thesudocommand.
A small gray block at the end of each line contains the number of entries in that event session.
Click a line to expand it.
We clicked the top line to see the details of the 24 entries in that session.
With a little scrolling, we can see the same events that we saw when we used thejournalctlcommand.
Usermary’s unexplained editing session on thefstabfile is quickly found.
We could have searched for “mary”, but that would include entries other than her use ofsudo.