A default Windows Server configuration is not inherently locked down and leaves important protection open and accessible to hackers.
Let’s take a look at how we can secure our web server!
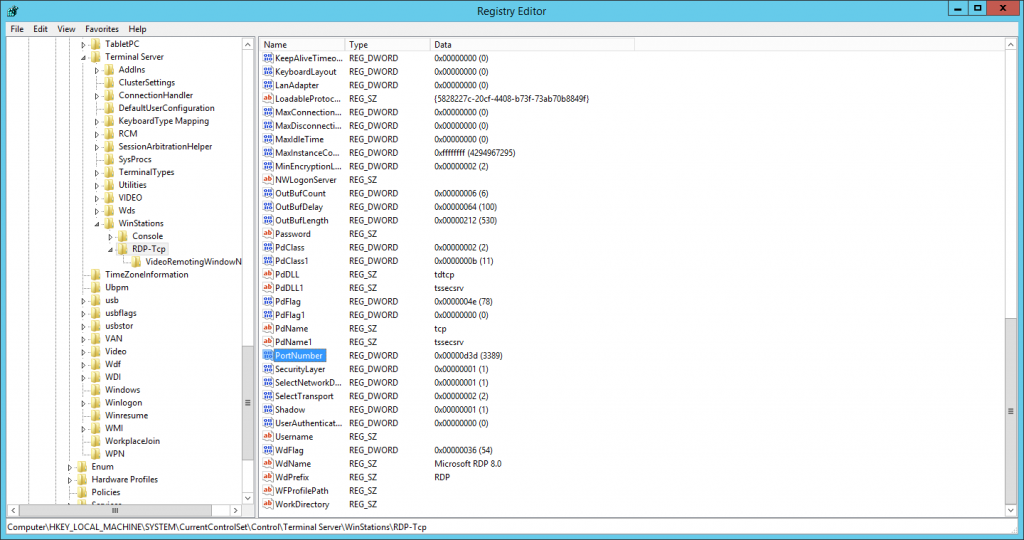
We can use this registry to make this necessary change.

Navigate to the following subkey, located at HKEY_LOCAL_MACHINESystemCurrentControlSetControlTerminal ServerWinStationsRDP-TcpPortNumber.
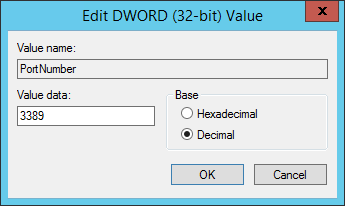
pop pop the subkey by double-clicking and change the Base punch in from Hexadecimal to Decimal.
Simply change this value from the default port of 3389, to your desired, unused, port.
For example, 3301.
Once saved, you must power cycle your server for the changes to take place.
This simple change can slow down and prevent hundreds or thousands of potential attacks on your server.
![]()
This brings us to our next point, updating system and user passwords.
Just like automated attacks against RDP, attackers will programmatically use software to guess passwords against default users.
One of the default users for Windows Server is the Administrator user.

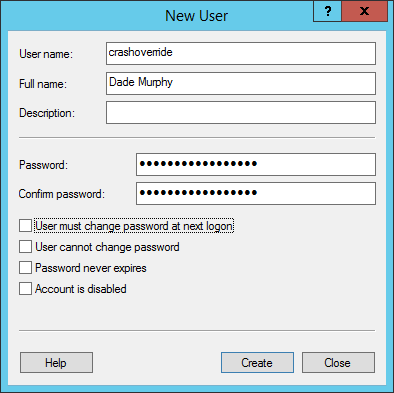
To get started, navigate to the local user and accounts management menu by searching your rig for lusrmgr.msc.
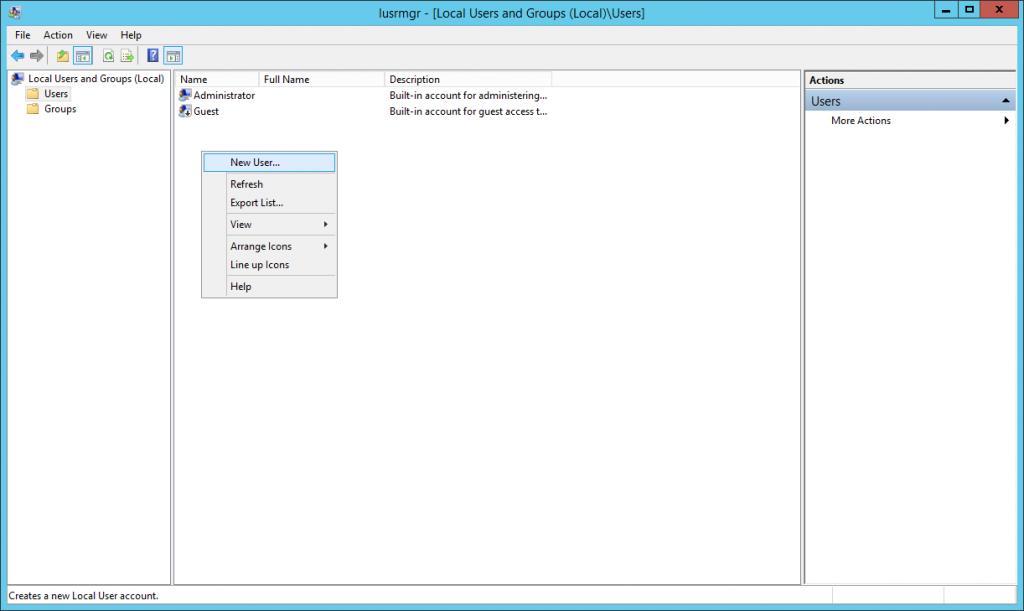
opt for Users group on the left actions-pane and right-click our main action pane to create a New User.
Your new username should be something unique and unexpected for an administrative user.
when you land entered the desired information, select Create to create the new user.
Now, find your new user in the User group, right-click and go to Properties.
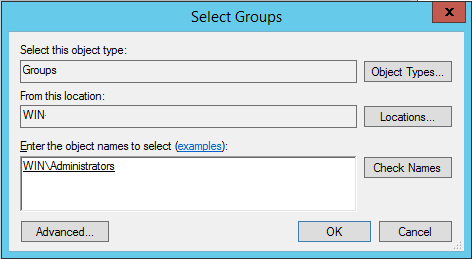
Click Add at the bottom of the menu.
The full administrators group will be identified and displayed.
If you are using Active Directory, you may type your domain and username for the administrator group.
Select OK and we can see our user is added to the Administrator users group!
Click OK to return to the Local Users and Groups manager.
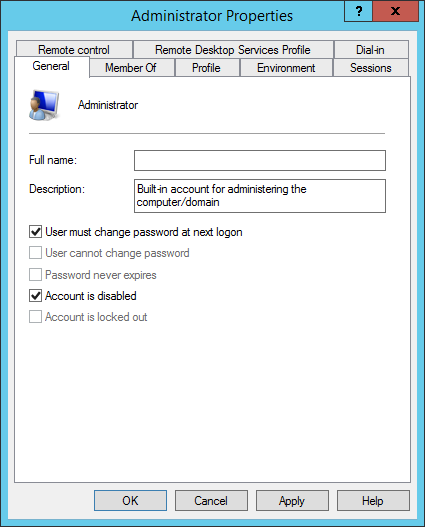
To do this, right-poke the Administrator, go to Properties, and check Account is Disabled.
You have now created a new administrator user and disabled the default admin account.
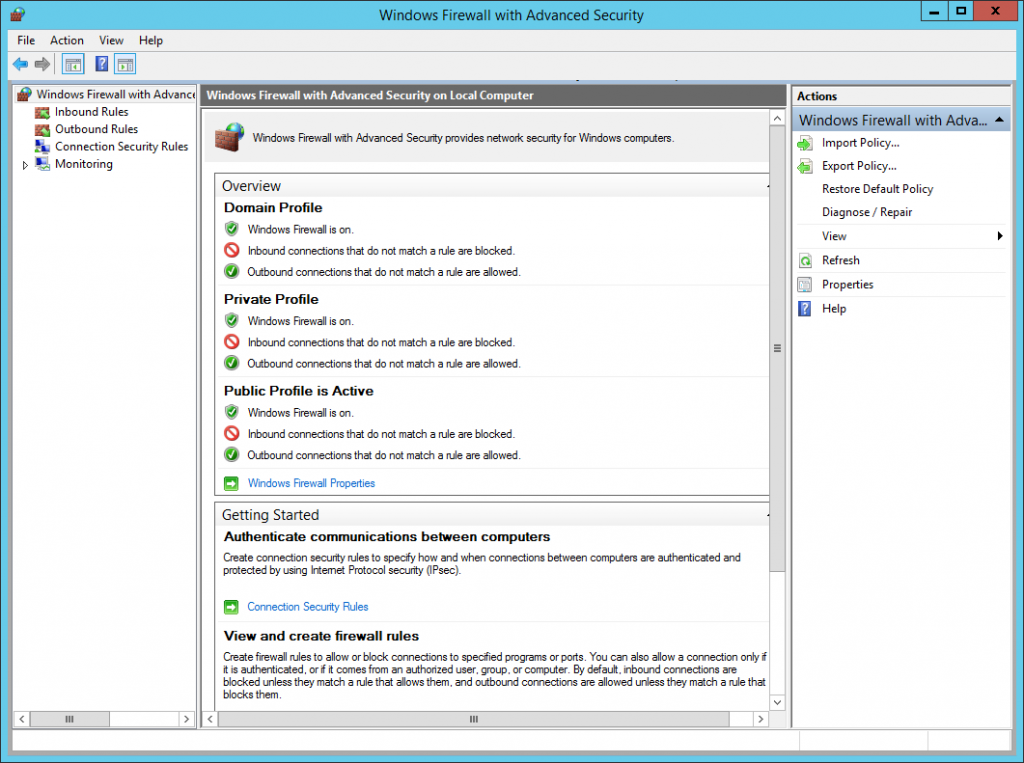
In most circumstances, firewalls should be configured to block all inbound connections unless otherwise specified.
This is a default setting for Windows Server but it is worth verifying on your server!
AV software should be up-to-date and patched often, as new threats emerge daily.
Incorporating brute-force detection and blocking software can also stop hackers in their tracks.
Security is a 24/7 365 job and hackers are always ready and executing attacks.