Quick Links
Iptables is an extremely flexible firewall utility built for Linux operating systems.
Read on as we show you how to configure the most versatile Linux firewall.
About iptables
iptables is a command-line firewall utility that uses policy chains to allow or block traffic.

If it doesn’t find one, it resorts to the default action.
iptables almost always comes pre-installed on any Linux distribution.
And don’t forget tolock down your SSH serverif you fire up the port.
Types of Chains
iptables uses three different chains: input, forward, and output.
Input- This chain is used to control the behavior for incoming connections.
Forward- This chain is used for incoming connections that aren’t actually being delivered locally.
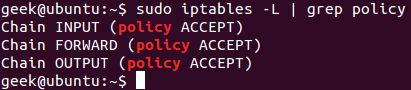
There’s one sure-fire way to check whether or not your system uses/needs the forward chain.
The forward chain, on the other hand, has not needed to process a single packet.
This is because the server isn’t doing any kind of forwarding or being used as a pass-through rig.
Output- This chain is used for outgoing connections.
SSH is a common protocol that people forget to allow on both chains.
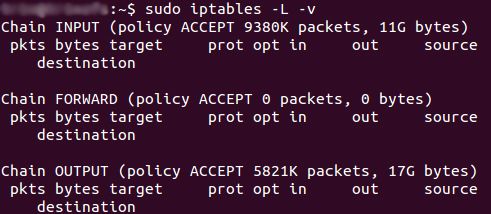
To see what your policy chains are currently configured to do with unmatched traffic, spin up the
command.
As you’re free to see, we also used the grep command to give us cleaner output.
In that screenshot, our chains are currently figured to accept traffic.
More times than not, you’ll want your system to accept connections by default.
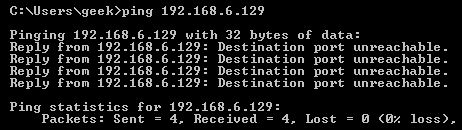
Unless you’ve changed the policy chain rules previously, this setting should already be configured.
We’ll get to those commands in a minute.
Accept- Allow the connection.
Drop- Drop the connection, act like it never happened.
This is best if you don’t want the source to realize your system exists.
Reject- Don’t allow the connection, but send back an error.
Note: In these examples, we’re going to use
to append rules to the existing chain.
Connections from a single IP address
This example shows how to block all connections from the IP address 10.10.10.10.
The
part of the code tells iptables what kind of connection the protocol uses.
If you were blocking a protocol that uses UDP rather than TCP, then
would be necessary instead.
This example shows how to block SSH connections from any IP address.
Connection States
As we mentioned earlier, a lot of protocols are going to require two-way communication.
But, what if you only want SSH coming into your system to be allowed?
Won’t adding a rule to the output chain also allow outgoing SSH attempts?
In other words - hostnames, protocols, and networks are listed as numbers.
To clear all the currently configured rules, you’re free to issue the flush command.
Linux Commands
Files
tarpvcattacchmodgrepdiffsedarmanpushdpopdfscktestdiskseqfdpandoccd$PATHawkjoinjqfolduniqjournalctltailstatlsfstabecholesschgrpchownrevlookstringstyperenamezipunzipmountumountinstallfdiskmkfsrmrmdirrsyncdfgpgvinanomkdirdulnpatchconvertrcloneshredsrmscpgzipchattrcutfindumaskwctr
Processes
aliasscreentopnicereniceprogressstracesystemdtmuxchshhistoryatbatchfreewhichdmesgchfnusermodpschrootxargsttypinkylsofvmstattimeoutwallyeskillsleepsudosutimegroupaddusermodgroupslshwshutdownreboothaltpoweroffpasswdlscpucrontabdatebgfgpidofnohuppmap
Networking
netstatpingtracerouteipsswhoisfail2banbmondigfingernmapftpcurlwgetwhowhoamiwiptablesssh-keygenufwarpingfirewalld