Quick Links
Summary
Isonline privacy a lost cause?
The words could have been tailor-made for the internet.
Typically, this leads to personalized advertising, but your data could be used for altogether more shady purposes.
Dave McKay/How-To Geek
Its a Debian-based Linux distro born out of the merger of two earlier privacy projects, Amnesia and Incognito.
Tails stands for “The Amnesiac Incognito Live System.”
It is designed to record nothing and to leak as little information as possible.
Dave McKay/How-To Geek
Tails runs in RAM and writes nothing to the hard drive.
Thats what the amnesiac part of its name refers to.
As for the incognito part, Tails forces all external web connection connections through theTor web connection.
Dave McKay/How-To Geek
Tails blocks any connection requests that attempt to side-step Tor and connect directly to the internet.
The Tor web link is avolunteer-run web link of nodes.
It encrypts and routes your connection into, through, and back out of the Tor online grid.

Dave McKay/How-To Geek
Your connection will be routed through at least three nodes.
Unlike regular internet traffic, your data packets are only labeled with where they need to go.
Normal data packets carry the details of their origin with them, too.
Dave McKay/How-To Geek
Tails is best used as a live distribution, booted from a USB flash drive.
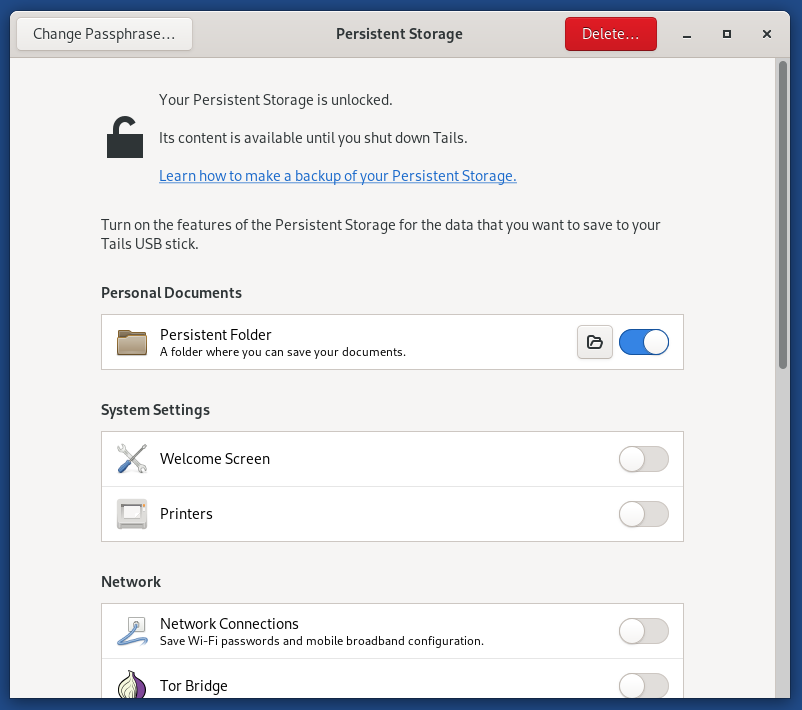
Everything in the persistent storage is automatically encrypted.
Theres the human element to consider.
Dave McKay/How-To Geek
That last link has to be made over the plain old, regular internet.
That means your traffic could be at risk of capture and analysis.
Even then, only use a single Tails session to conduct a single activity.
Dave McKay/How-To Geek
If youre going to transfer files or images, clean the metadata from them first.
Tails includes a metadata cleaner tool for this purpose.
Storing information on your USB drive, even though its in your persistent encrypted storage, is risky.
They won’t know what you did, but they’ll know you used Tor to do it.
During the boot process, hit the keystroke(s) that opens up your Boot Menu.
Computers usually display a message telling you the key you better press, and when to press it.
These messages are usually fleeting, so you might need to boot the computer twice.
Once to read the message, and once more to hit the key.
your gear will boot up into Tails.
Using Tails
Tails boots into a welcome screen that allows you to set your keyboard layout.
it’s possible for you to change your keyboard layouts later using the usual GNOME options software.
Theres a separate Persistent Storage management program as well.
The first thing Tails offers to do is to connect to the Tor internet automatically.
Launching the Tor web client gives you a secure web web client.
The uBlock Origin content filter and ad blocker extension is installed by default.
You also find Persistent Storage in the dock.
This is an app that lets you manage your persistent storage.
However, Tails is the most popular operating system of its bang out, and with good reason.
It is constructed from the ground up with privacy and anonymity in mind.
And it can deliver that, as long as you use it with awareness.
Its like a cloak of invisibility.
On the face of it, its fantastic.
But you oughta double-check its pulled down to the ground so your feet dont show.